Maintaining visibility into DNS-related activities is crucial for organizations to ensure the security and performance of their web-based applications. Cloud engineering teams must use tools to effectively monitor and analyze DNS queries to protect from DNS-based attacks and optimize performance for genuine requests. DNS Query logging for Amazon Route 53 hosted zones addresses this challenge … Continue reading Enable Domain Name System (DNS) query logging for Amazon Route 53 hosted zones using Terraform
Tag: application load balancer
Attach AWS WAF to load balancer using Terraform and GitHub Actions
Public-facing load balancers are vulnerable to attacks, including DDoS, SQL injection, cross-site scripting (XSS), and bot attacks. These attacks can degrade the load balancer's performance, rendering it unavailable to legitimate users and negatively impacting business operations. AWS Web Application Firewall (WAF) is a service designed to protect resources like load balancers, Amazon CloudFront distributions, API … Continue reading Attach AWS WAF to load balancer using Terraform and GitHub Actions
Create infrastructure to host an Amazon ECS Service using Terraform
This is the first part of an umbrella note in which I describe how to create and deploy an Amazon ECS service using Terraform and GitHub Actions. The cloud engineering team must provision particular AWS cloud services before hosting a container in Amazon ECS. In this note, I list all the required AWS services, their … Continue reading Create infrastructure to host an Amazon ECS Service using Terraform
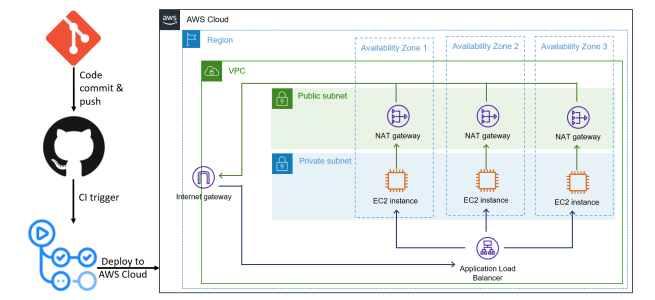
Add an application load balancer to Amazon EC2 instances in a private subnet
In this note, I create a highly available environment using Amazon EC2 instances spread over multiple availability zones attached to an application load balancer. I also have a link to my GitHub repository with the code. In the past, I wrote a note on how to toggle traffic between three EC2 instances in three availability … Continue reading Add an application load balancer to Amazon EC2 instances in a private subnet