In the past, I've written a note explaining the process of deploying the Terraform IaC configuration into an AWS account using GitHub Actions. In this note, I extend that functionality and deploy the same Terraform IaC configuration across multiple AWS accounts using Terragrunt and GitHub Actions. Before we delve deeper, let me briefly explain the … Continue reading Deploy Across AWS Accounts Like a Pro: Terragrunt, Terraform, and GitHub Actions
Tag: Terraform
Add an application load balancer to Amazon EC2 instances in a private subnet
In this note, I create a highly available environment using Amazon EC2 instances spread over multiple availability zones attached to an application load balancer. I also have a link to my GitHub repository with the code. In the past, I wrote a note on how to toggle traffic between three EC2 instances in three availability … Continue reading Add an application load balancer to Amazon EC2 instances in a private subnet
Implement pull request-based workflow using Terraform, Infracost, Checkov, and GitHub Actions
The software development process has continuously evolved over the past several years. The evolution process continued with the wide-scale availability of cloud platforms like AWS and Azure. We realized the practice of infrastructure as code (IAC) when the development practice of coding was merged with the operations practice of creating and managing cloud infrastructure. Then, … Continue reading Implement pull request-based workflow using Terraform, Infracost, Checkov, and GitHub Actions
Estimate AWS Cloud resource cost with Infracost, Terraform, and GitHub Actions
There are two broad aspects to running a successful business. These are (a) creating a product that generates revenue and (b) managing the product cost that is lower than the revenue. E.g., if the product generates $100 in revenue and costs $90, then the business can survive because it is generating a 10% profit margin. … Continue reading Estimate AWS Cloud resource cost with Infracost, Terraform, and GitHub Actions
Create AWS Secrets Manager secret using Terraform secure variables and GitHub Actions secrets
A little while back, I encountered an exciting use case requiring me to use GitHub Actions secrets. The use case was to create an AWS Secrets Manager secret resource using Terraform in a CI/CD pipeline. An AWS Secrets Manager secret is a resource to store secure credentials. In the past, I created an AWS Secrets … Continue reading Create AWS Secrets Manager secret using Terraform secure variables and GitHub Actions secrets
Automate Terraform configuration scan with Checkov and GitHub Actions
Terraform enables developers to create cloud resources via a few lines of code. Hence, these developers must write code that is easy to understand and follows security best practices. Moreover, following best practices becomes a habit if there is a system to keep that in check. Checkov is a proven static analysis tool that checks for standard best practices in your … Continue reading Automate Terraform configuration scan with Checkov and GitHub Actions
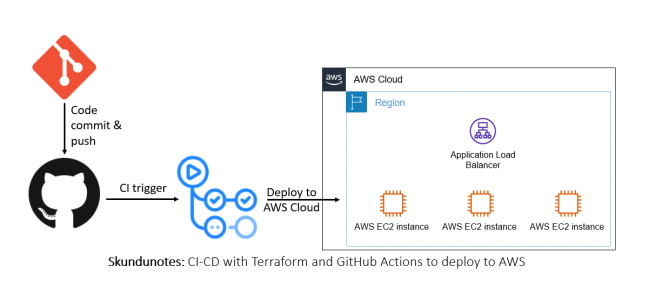
CI-CD with Terraform and GitHub Actions to deploy to AWS
GitHub Actions is a CI/CD tool that can automate the provisioning of AWS resources using Terraform. Previously, I wrote a detailed post explaining the concepts associated with using Terraform to create an application load balancer that you can read here -add an application load balancer to Amazon EC2 using Terraform. In this note, I further … Continue reading CI-CD with Terraform and GitHub Actions to deploy to AWS
A detailed guide to securely integrating Amazon Managed Grafana with Terraform
Over the last couple of months, I worked extensively on Amazon Managed Grafana to create dashboards for observability. In the course of automating the deployment using Terraform and a CI-CD system, I learned about a few challenges and identified solutions. I'm sharing my learnings in this note so that you do not make the same … Continue reading A detailed guide to securely integrating Amazon Managed Grafana with Terraform
Create an Amazon Managed Grafana dashboard using Terraform and Azure Pipelines
Recently I came across a use case where I was required to create Grafana dashboards using the Terraform Grafana provider. Although it did not sound too complex, it soon became once I started automating the process using Azure Pipelines. In this note, I documented the challenge and the solution. Before diving deeper, an Amazon Managed … Continue reading Create an Amazon Managed Grafana dashboard using Terraform and Azure Pipelines
Create an Amazon Managed Grafana workspace using Terraform
In this note, I describe the steps to provision a new Amazon Managed Grafana workspace using the AWS Terraform provider. Grafana is an open-source observability tool to visualize data. It provides charts, graphs, and alerts for the web when connected to supported data sources. Per AWS-Docs, Amazon Managed Grafana is a fully managed and secure … Continue reading Create an Amazon Managed Grafana workspace using Terraform